Creating Custom Notable Event in Azure Security Center
In Azure Security Center you can use the Events dashboard to see the security events (including Windows Firewall) collected over time: 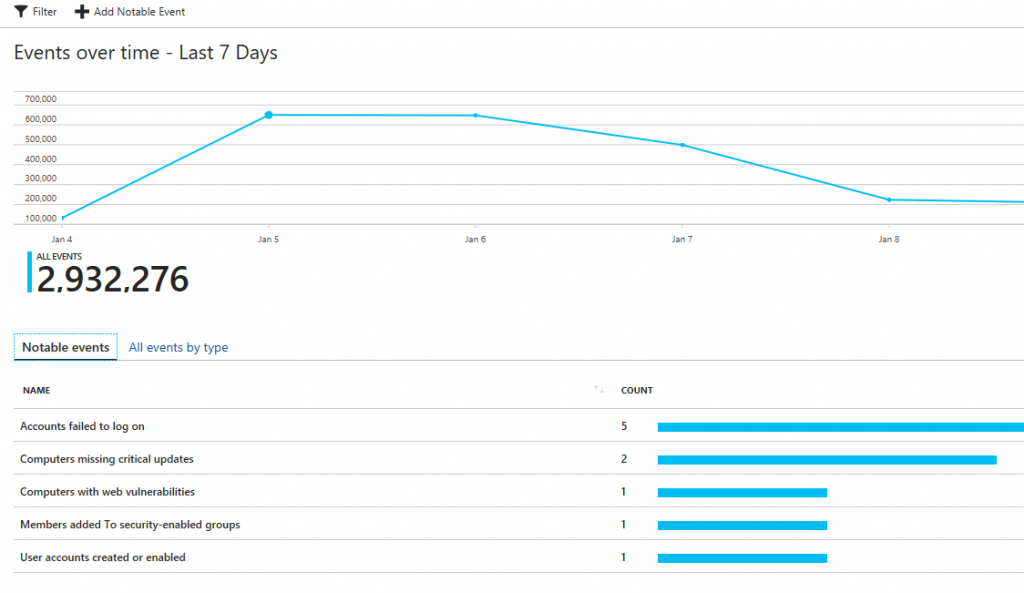
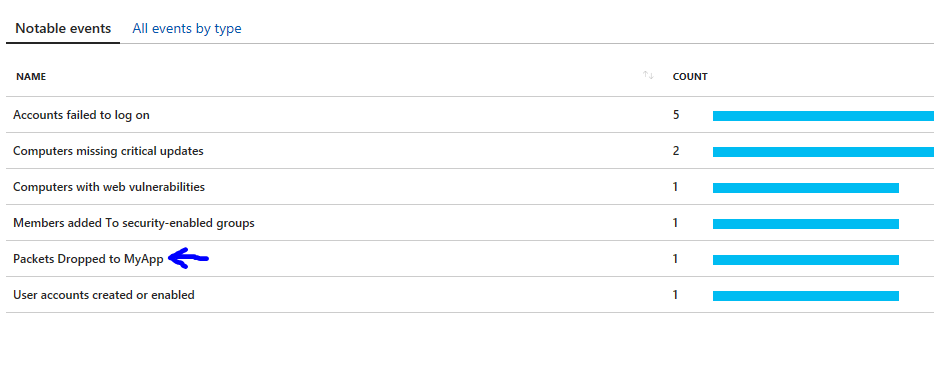
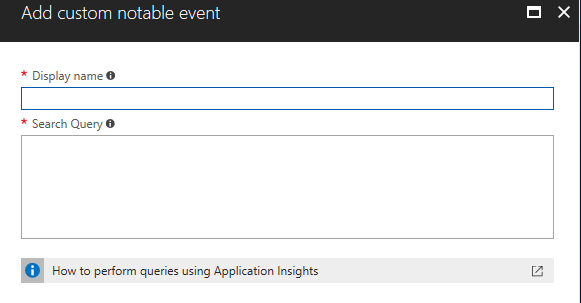
The visualization of security events over time can be very useful for you to observe some patterns, and to have a snapshot of the environment. You can also use this information when performing an investigation, for example to understand for how long certain event is taking place on a particular system. While Security Center shows the most relevant security events, you can also customize and create your own notable event. Let’s say you have an application that uses UDP on port 58343, and you want to monitor this application for packets dropped. In this case you don’t want to raise alerts (if you wanted, you should create a custom alert), you just need to have historical data regarding the amount of dropped packets. To accomplish this task, click Add Notable Event, and type the information in the Add custom notable event page:
For the purpose of this example, I will call this notable event Packets Dropped to MyApp, and will add the following query in the Search Query field:
WindowsFirewall
| search "DROP"
| where DestinationIP == "192.168.1.47"
| where DestinationPort == "58343"
When you finish, click OK to create, and the dashboard will now show you custom notable event: