"No identities found" adding users from Azure Active Directory to Azure DevOps
[Updated Feb 28, 2019]
Scenario
- Your Azure DevOps org is backed by Azure Active Directory (AAD)
- You are the a member of the Project Collection Administrators group inside Azure DevOps
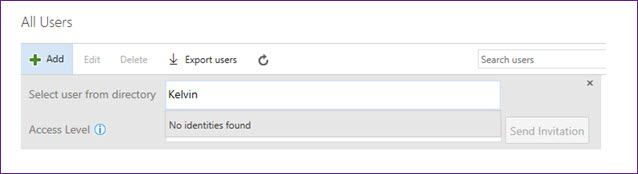
- You are trying to add users to Azure DevOps either on the Users Hub or in Security
- You type in the name of a user who you know is in the AAD but you are told No identities found
Cause
You're probably a guest in the AAD that backs Azure DevOps org, rather than a member. By default AAD guests cannot search the AAD in the manner required by Azure DevOps.
Resolution
First, check to see if you are an AAD guest:
-
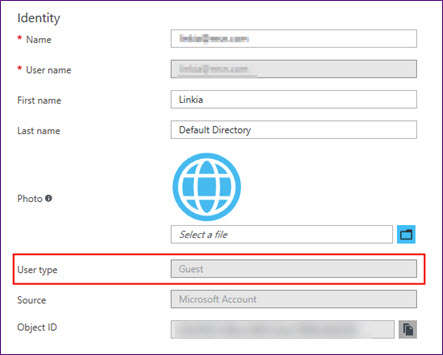
- Go to the Settings section of your Azure DevOps org (Dev.Azure.com/<org>/_settings) and look at the Azure Active Directory section. Make a note of the tenant that backs your Azure DevOps org.
- Log into portal.azure.com and check your user profile in the tenant from step 1. Check the User type value as seen below.
If you are an AAD guest you have a few options:
- Have another Azure DevOps org admin - someone who is not an AAD guest - manage the users in Azure DevOps for you. Members of the Project Collection Administrators group inside Azure DevOps can administer users, as can the owner.
- Have the AAD admin(s) remove you from the AAD and re-add you, making you an AAD member rather than a guest when they do. See "Can Azure AD B2B users be added as members instead of guests? " on /en-us/azure/active-directory/active-directory-b2b-user-properties.
- Change the User Type of the AAD guest using Azure AD PowerShell. This is an advanced topic and is not advised, frankly, but it does work and allows the user to query AAD from Azure DevOps org thereafter:
Convert AAD UserType from Guest to Member using AAD PowerShell
Prerequisites for the user making the UserType change:
- *Must* use a Work\School Account (WSA): a native user in AAD. You cannot do this with a Microsoft Account.
- *Must* be Global Admin in the AAD
I recommend you create a brand new (native) AAD user who is a Global Admin in the AAD then perform the steps below with that user. From experience helping people through this I know you run a high risk of problems, usually caused by connecting to the wrong AAD, if you don't. Save yourself the headache and just make a new user. You can delete it when you're done, after all.
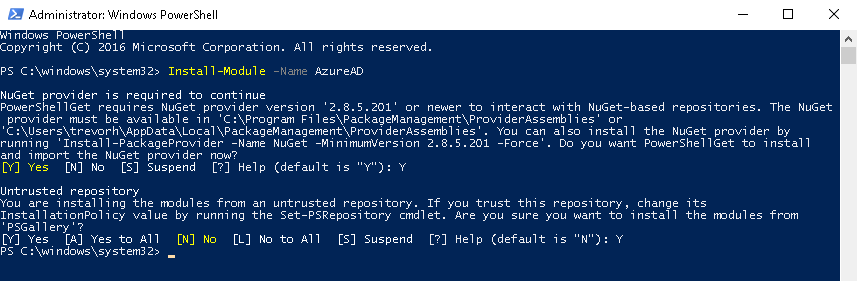
- Open an Administrative Windows PowerShell prompt
- Execute Install-Module -Name AzureAD. This will download the Azure Active Directory PowerShell for Graph from the PowerShell Gallery. You may see prompts about installing NuGet and untrusted repository as pictured below. If you run into issues please review the system requirements and information at the Azure Active Directory PowerShell for Graph page.
- Once the installation completes, execute Connect-AzureAD. You will be prompted to log in to the Azure AD. Be sure to use an ID that meets the criteria above.
- Execute Get-AzureADuser -SearchString "<display_name>" (where <display_name> is part of or the entire display name for the user as seen inside the Azure portal). The command will return four columns for the user found - ObjectId, DisplayName, UserPrincipalName, UserType - and UserType should say "Guest".
- Execute Set-AzureADUser -ObjectID <string> -UserType Member, where <string> is the value of ObjectId returned by the previous command. This should set the user to Member status.
- Execute Get-AzureADuser -SearchString "<display_name>" again to verify the UserType has changed. You can also verify this in the Azure Active Directory section of the Azure Portal.
While not the norm, we have seen it take several hours or even days before this change is reflected inside Azure DevOps. You may expedite it by signing into Visual Studio Profile (aka.ms/VsProfile) using the UPN that was just changed in AAD (when in profile, be sure to select the AAD in which the changes were made). If it doesn't fix your Azure DevOps issue immediately, give it some time and keep trying.
HTH,
Trev
Please see these posts for additional info:
- <blogs.technet.com/b/ad/archive/2014/08/15/prepping-for-new-management-features.aspx>
- See /en-us/azure/active-directory/active-directory-users-assign-role-azure-portal for guidance on how to add someone to the AAD Global Admin role.
- Azure Active Directory PowerShell for Graph