NAV and Multi Factor Authentication (MFA)
Over the last weeks I have gotten an increasing number of inquiries around MFA. To be honest, I had never tried to setup MFA before, but that didn't stop me from answering.
My typical answer would be the following:
NAV itself does not have any knowledge about multi factor authentication, but we do support claims based authentication through authentication providers and if these authentication providers are setup for MFA, then NAV should support MFA through the authentication provider.
Having answered the same thing a number of times, I decided it was time to try it out.
Setting up a NAV DEMO environment
As always, I started out by creating a NAV DEMO environment using https://aka.ms/navdemodeploy and in the section on Office 365 I added an Office 365 administrator email address and password. Whether you want to create the portal or not does not matter.
After waiting for some time your landing page will reveal that the installation is Complete and you can get going.
Two different authentication methods
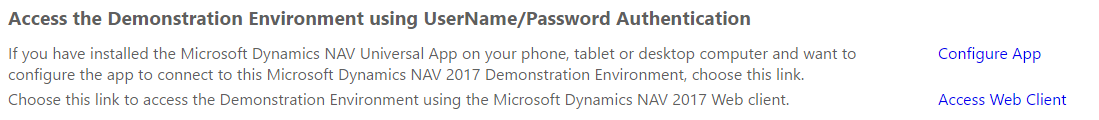
On the landing page for your demo environment you will find two sections talking about authentication. One talking about how to access your demo environment using UserName/Password Authentication:
and one talking about how to access your demo environment using AAD or O365 authentication:
You CANNOT setup MFA for the UserName/Password authentication model. You can remove this option of authentication if you like and ONLY have AAD / O365 authentication,
You CAN setup MFA for AAD / O365 authentication and you do NOT have to tell NAV anything about that. It is your little secret, and NAV just supports it.
So basically when we decide to out-source the authentication to somebody else, they can do it as they want to - as long as they bring a claim to us, describing who the user is, which we can map to a user in the NAV user table (the Authentication E-Mail address).
AMFA (Azure Multi Factor Authentication)
Before starting to setup MFA, you should read this.
And, if you want to read more about how it actually works, go here.
If you just want to set it up, follow this process:
Navigate to https://portal.office.com with the Office 365 administrator email and password, which you used to setup your demo environment.
Click the Waffle Icon (top left corner) and go to Admin:
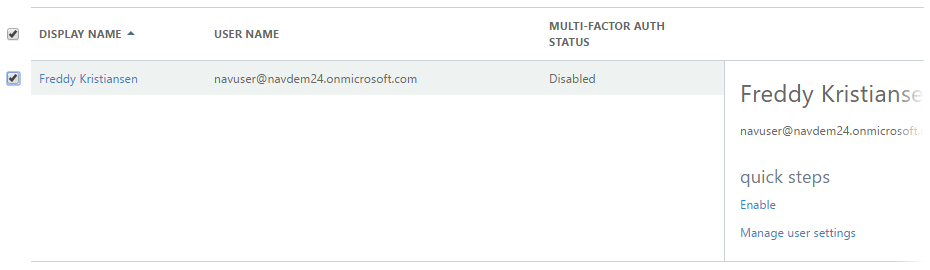
Select Users, Active users:
Under More, select Setup Azure multi-factor auth 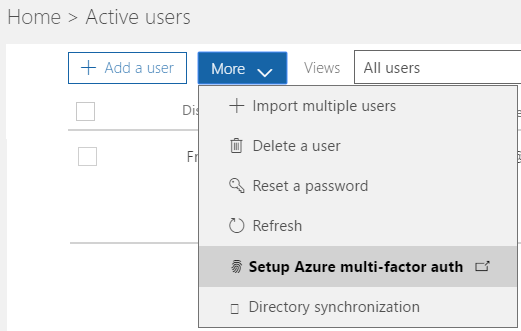
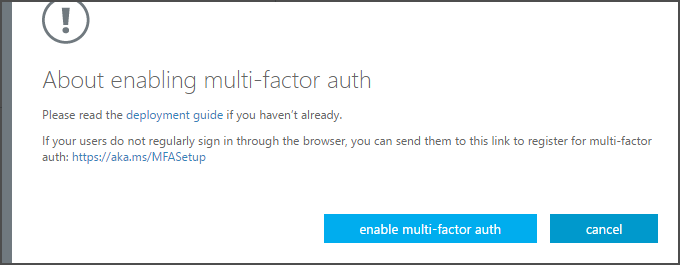
Select the user(s) you want to enable for MFA and select Enable under quick steps
In the dialog that pops up, select enable multi-factor auth
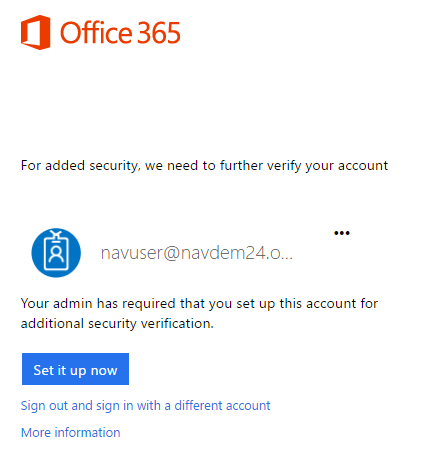
After this, when you sign out and back in you will be asked to setup MFA:
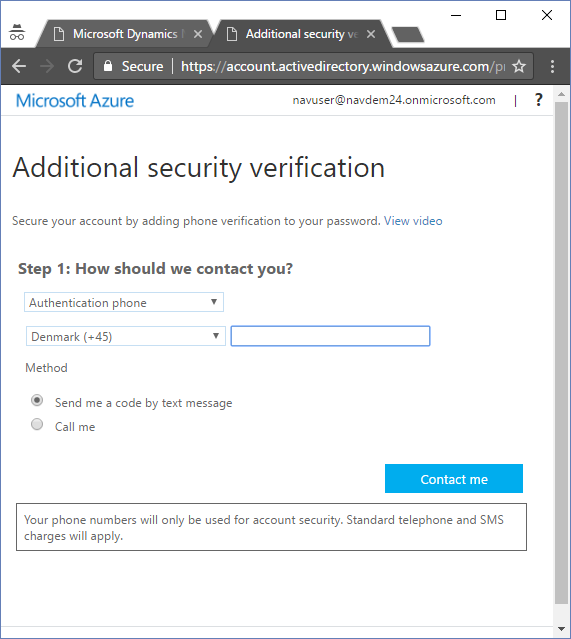
When you click Set it up now, you will be taken to the additional security verification setup web site:
You can also get to this web site by navigating to https://aka.ms/MFASetup and select profile -> Additional security verification.
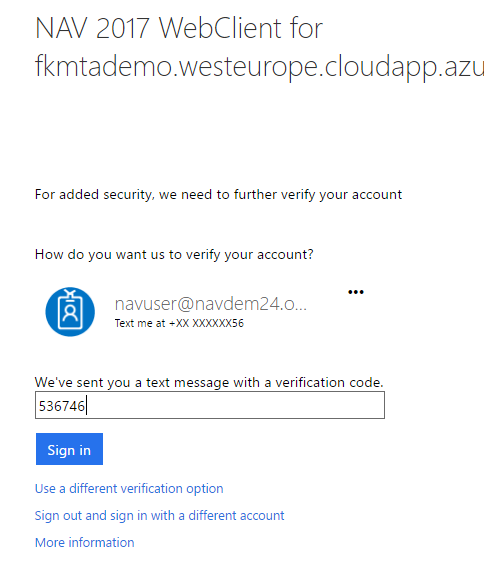
After the setup of MFA is complete, locate the URL on your landing page for accessing the Web Client using AAD or O365 authentication and after providing your password you will get a text message and will be asked to provide that.
So, as you can see MFA does not require any changes in NAV, it is something that is handled by the authentication provider and there is actually nothing you can setup in NAV for that.
I have also tested that the Windows Client works with the same setup.
Other authentication providers
If you are using ADFS or other authentication providers supported by NAV (we do not have an exhaustive list) then it is the same deal. We redirect to the authentication provider for authentication and if that would use any number of authentication validations before returning an authentication email in a claim to NAV, we don't really care:-)
Enjoy
Freddy Kristiansen
Technical Evangelist