Windows XP SP2 Study notes
Few months ago when Windows XP Service Pack 2 launched, I prepared a study notes for myself to summarize the changes in it in a few pages. I got requests from my friends to share it so I'm putting it here to be available to all
Windows XP SP2
Table of content:
-
- How to enable remote administration to windows xpsp2
- How to enable remote debugging with SP2
- ASPNET Cannot Serve Pages When Running on XPSP2
- ASP.NET session state pages might not work on XPSP2
- ASP and ASP.NET may not work if IIS is installed After Windows XP SP2
- Enabling ASP.NET Transactions with Windows XP SP2
- Enabling COM Logging to assess permissions for DCOM Launch/Activation with Windows XP SP2
- The NET SEND command may not work correctly on a computer that is running Windows XP Service Pack 2
- You may not be able to connect to an instance of SQL Server that is configured to use the TCP/IP server network library on a computer that is running Windows XP Service Pack 2
Introduction
The main Modification areas of XP SP2
Network protection
Memory protection
Email security
Browsing security
In addition to the security technology enhancements, Microsoft has also added Improved Computer Maintenance in SP2 that includes:
* "silent" automatic updates for consumers.
* intelligent download of update data on low-bandwidth connections.
* a new Security Center to centralize patch management.
* better security options in Windows Installer.
* a more resilient version of Microsoft's Windows Update site to increase availability and resist denial-of-service (DOS) attacks.
If you have any suggestions or modifications please email me 
Network protection
• Alerter and messenger services.
stopped by default. You need to open it manually see (you can’t use net send command without the messenger service) https://go.microsoft.com/fwlink/?LinkId=25974
• WebDAV redirector 
The WebDAV Redirector (DAVRdr) allows computers running Windows XP to use WebDAV (Web-based Distributed Authoring and Versioning) servers, such as Windows SharePoint Services and MSN Communities, as if they were standard file servers. It consists of a kernel component that connects to a Windows NT remote file system stack, and a user-level component (Web client service) that translates file system requests into WebDAV requests.
SP2 by default disable basic authentication for the DAVRdr
You can enable the basic authentication by adding this registry key and add a non zero value to it
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \WebClient\Parameters\UseBasicAuth (DWORD)
• WinInet (disable basic authentication over clear network)
With Windows XP Service Pack 2, there are two ways to block the use of Basic Authentication over clear (unencrypted) channels:
1. Create the following registry key and set it to a non-zero value.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows \CurrentVersion\ Internet Settings\DisableBasicOverClearChannel (DWORD)
This prevents WININET from attempting to use BasicAuth unless the channel is secured (HTTPS or SSL).
2. The application can disable the use of BasicAuth for its connections by setting the AUTH_FLAG_DISABLE_BASIC_CLEARCHANNEL flag (0x4) in the value supplied in the call to InternetSetOption using INTERNET_OPTION_AUTH_FLAGS.
• Windows firewall
Stateful firewall
for IP v4 and IP v6 as well.
SP2 turns on windows firewall and start it earlier in the windows startup process.
Any listeners (servers) on the machine will be disabled.
description of windows firewall in https://support.microsoft.com/default.aspx?scid=kb;EN-US;320855
There’s a default boot-time policy applied to the windows firewall in the boot time to enable the firewall to start early in the boot process without any conflicts with the default services like DNS and DHCP or any communications with the domain controller. (Any others will be denied)
The configuration can be done globally for all network connections or per connection.
The user can create to firewall policies 1) when the computer connected to the work intranet 2) when the computer not
Multiple profiles applied to the computers that joined domain only.
Service Pack 2 also includes new Group Policy Objects (GPOs) to allow network administrators to manage Windows Firewall policy in the corporate environment. These GPOs include Operational mode (On, Off, or On with No Exceptions), Allowed Programs, Opened Ports (static), ICMP settings, and Enable RPC. These can be configured in both the corporate and standard profiles.
Applications permissions lists (Windows firewall permissions lists)
It can be set programmatically or visually (by administrators only) and for the application that in the permission list , the windows firewall will open the required ports with out running with administrator user account
Administrators can also manage the Windows Firewall Permissions List using the Netsh command-line utility
RPC has a problem since there’s many servers that listen to RPC ports and these ports are dynamically determined at runtime.
Since so many RPC servers are included with Windows XP, and since most of them run using the same process image file name (Svchost.exe), Windows Firewall adopts a different approach for RPC servers. When opening a port, a caller might claim that the port is to be used for RPC. Windows Firewall will only accept this claim if the caller is running in the Local System, Network Service, or Local Service security contexts. Windows Firewall supports a profile level flag that enables RPC ports to be opened even if the caller is not on the Windows Firewall Permissions List.
• This is stored in the registry as a REG _DWORD value named PrivilegedRpcServerPermission under the profile key. The values correspond to the NET_FWV 4_SERVICE_PERMISSION enumeration:
• NET_ FWV 4_SERVICE_BLOCK = 0. RPC servers are only allowed to open ports if they are on the Windows Firewall Permissions List.
• NET_ FWV 4_SERVICE_ALLOW_LOCAL = 1. If an RPC server is not on the Windows Firewall Permissions List, the port will be opened, but only accept network traffic from the local subnet.
• NET_ FWV 4_SERVICE_ALLOW_ ALL = 2. If an RPC server is not on the Windows Firewall Permissions List, the port will be opened for network traffic from any subnet.
For more information
https://msdn.microsoft.com/security/productinfo/XPSP2/networkprotection/firewall.aspx
Developer implication
All IPv4 outbound connections allowed by default.
Notes
• When a computer initiates a TCP connection to a remote computer, Windows Firewall allows TCP traffic to the port from which the TCP connection was initiated only from the Internet Protocol (IP) address to which the TCP connection was initiated.
• When a computer sends UDP packets, Windows Firewall allows UDP to the port from which the UDP packets were sent from any IP address for 90 seconds.
• Unicast responses to multicast and broadcast traffic are allowed through Windows Firewall for 500 milliseconds if the responses are to the port from which the multicast traffic was sent and are from IP addresses on the same subnet as the computer. A setting in the firewall controls this behavior, which is enabled by default for the firewall's other profile.
Examples
• Surfing the Web using Microsoft Internet Explorer
• Checking e-mail in Outlook Express
• Chatting in MSN Messenger or Windows Messenger
IPv4 inbound connection is not allowed by default. You application needs to be added to the permission list of the firewall.
You can use the ICF APIs documented here
https://msdn.microsoft.com/library/default.asp?url=/library/en-us/ics/ics/icf_plus_intro.asp
you will use INetFwV4AuthorizedApplication COM interface or the NetFwV4AuthorizedApplication COM class to implement this and you can also use .NET language through COM interop.
For more information
https://msdn.microsoft.com/security/productinfo/XPSP2/networkprotection/firewall_devimp.aspx
• RPC interface restrictions
RestrictRemoteClients registry key
\\HKLM\SOFTWARE\Policies\Microsoft\Windows NT\RPC\
This restricts anonymous access to the RPC interfaces.
Developer implications
EnableAuthEpResolution registry key
\\HKLM\SOFTWARE\Policies\Microsoft\Windows NT\RPC
For the application that uses dynamic RPC endpoint there’s an interface called RPC Endpoint Mapper interface. This registry key restricts anonymous access to this interface.
Developer implications
None
New RPC interface registration flags
Developer implications
Any developer wants to register RPC interface should take care of this change.
• DCOM Security enhancements
Computer-wide restrictions
Now there’s a computer-wide control list that must be passed before any activation/Access process happened to the COM remotely.
So I can identify the minimum privileges to connect to COM in windows XP SP2 machine regardless the settings of specified server.
Developer implications (to stop this feature)
Granular COM permissions
There are two types of permission ACL
Launch and Activation permissions
I can choose specific users to do the following
Local Launch (LL)
Remote Launch (RL)
Local Activate (LA)
Remote Activate (RA)
Access Permissions
I can choose specific users to do the following
Local Calls (LC)
Remote Calls (RC)
And all that exposed through the administration MMC of the COM+
See the table in https://msdn.microsoft.com/security/productinfo/XPSP2/networkprotection/granular_com_permissions.aspx to see the default machine-level permissions
Developer implications
https://msdn.microsoft.com/security/productinfo/XPSP2/networkprotection/granular_com_permissions_devimp.aspx

• Blue tooth support
In sp2 there’s support for the blue tooth technology that include
• Connect a Bluetooth device to a computer
• Create a wireless desktop with a Bluetooth keyboard and mouse
• Transfer files to or from a Bluetooth device
• Print to a Bluetooth printer
• Connect to a computer network or the Internet through a Bluetooth mobile phone.
• Set up an Internet Protocol (IP) connection to the Internet through a Bluetooth mobile phone.
If the appropriate Microsoft or third-party software programs are installed on Windows XP, you can also perform other operations with Bluetooth devices, such as:
• Synchronizing contacts and calendars with a Bluetooth mobile phone or personal digital assistant (PDA).
• Reading coordinates from a GPS receiver.
This release also has support for these Bluetooth profiles:
• Personal Area Networking (PAN). Enables IP connections over Bluetooth wireless technology.
• Hard Copy Replacement Profile (HCRP). Enables printing.
• Host Interface Device (HID). Enables Bluetooth keyboards, mice, and joysticks.
• Dial-Up Networking (DUN). Enables Bluetooth mobile phones to work as modems.
• Object Push Profile (OPP). Enables file transfers.
• Virtual COM ports (SPP). Enables legacy programs to communicate with Bluetooth devices.
In addition, these Bluetooth features are included:
• Selective suspend. Reduces the power consumption of Bluetooth transceivers connected to the computer by means of a Universal Serial Bus (USB) connection.
Boot-mode keyboards. Enables specifically-configured Bluetooth keyboards to work with the BIOS.
If no Bluetooth transceiver is present on the system, there is no change to the system's behavior. When a Bluetooth device that is approved by the Windows Hardware Quality Labs (WHQL) is present, Bluetooth support is enabled.
New Memory Protection
Execution protection
Also known as NX or (no execute)
Prevent code execution from data pages. Forced developers to avoid executing code out of data paged without explicitly mark it as executable
Based on hardware feature in the processor. The processor can raise exception when executing instructions in data page.
Only processors that support this right now is AMD K8 and Intel Itanium
Developer implications
Things related to virtualAlloc() function
https://msdn.microsoft.com/security/productinfo/XPSP2/memoryprotection/exec_imp.aspx
Improved Email Security
Attachment Execute Service
Outlook express use its own algorithm to identify the dangerous attachments and outlook as well. The Attachment execute service will unify identifying the dangerous of attachment through all Microsoft and third party products.
Developer implications
Any developer who write email or chat client should use this service to identify the dangerous attachments.
Third party applications don’t need to make trust decisions. The Attachment Execute Service will make these decisions configurations and capabilities of the computer and give the users message telling them how to reopen the files including information about the application that will be used as a handler for that file
The AES gives the attachments risk rating based on the extension, content Type, registered handlers and others.
The risk rating then mapped into a policy that is checked using the familiar IE zones (restricted, Internet, Intranet, local and trusted)
The programmatically entry point for this service is the IAttachmentExecute interface (COM). It include these functions
CheckPolicy() , PromptUser() , Execute() , Save()
The check policy need to collect evidences about the attachment so the client application need to call these functions before the checkPolicy() function
SetFileName()
SetLocalPath()
SetReferrer()
SetSource()
The evidence collected for the attachment is also saved with the attachment when it’s executed at a later time.
More information on https://msdn.microsoft.com/library/default.asp?url=/library/en-us/shellcc/platform/shell/reference/ifaces/iattachmentexecute/iattachmentexecute.asp.
Enhanced Browsing Security
Locking down the local machine zone
The SP2 put more restriction on the html pages that executed under the local machine zone. (you will not see this zone in IE zones)
It does these settings
URLACTION_ACTIVEX_ RUN resolves to Disallow.
URLACTION_ACTIVEX_OVERRIDE_OBJECT_SAFETY resolves to Disallow.
URLACTION_SCRIPT_ RUN resolves to Prompt.
URLACTION_CROSS_DOMAIN_ DATA resolves to Prompt.
URLACTION_BINARY_BEHAVIORS_BLOCK resolves to Disallow.
URLACTION_JAVA_PERMISSIONS resolves to Disallow.
So any ActiveX control will not run and any code will ask the user first before executing.
We can stop or start these restrictions by editing registry keys (see https://msdn.microsoft.com/security/productinfo/XPSP2/securebrowsing/locallockdown.aspx )
Developer implications
Locking down the local machine zone is enabled only to the IE and explorer.exe you need to register your application to make sure that there’s any malicious code can run through it.
Applications that host IE, these restrictions enabled for it.
If you experience problem with your DHTML code in the local machine zone then you need to save it as HTA (HTML Application) but be careful as it will run with full privileges and it can be dangerous
If the web page downloaded from a web site you can add this tag to it
<!-- saved from url=(0023)https://www.contoso.com/ -->
So the IE will apply the security settings of this web site’s zone.
Another alternative is to use web browser control inside your application to run your ActiveX and code.
For more information
https://msdn.microsoft.com/security/productinfo/XPSP2/securebrowsing/lockdown_devimp.aspx
Popup Manager
• Unwanted popup will be blocked.
• Pop-ups that initiated by user clicks will not be blocked.
• Users and administrators can let specific domains to initiate programmatic pop-ups
• Popup manager is turned off by default.
• Sites in the trusted sites’ zone and intranet zone will not be blocked.
• You can configure it in the security tab in the “internet options”
• At the first popup the popup manager give you a prompt that asks you to enable popup manager
• When a popup is blocked a notification is appeared in the status bar and a sound played.
If the user clicked on this notification, option window appears with these options
1. Show Blocked Pop-up Window. Reloads the pop-up window.
2. Allow Pop-up Windows from This Site.Adds the current site to the Allow list. Sites can be added to this list in a setup application by an administrator.
3. Block Pop-up Windows. Toggles Pop-up Manager on and off.
4. Pop-up Window Options. Opens the Pop-up Window Managementwindow.
• Regardless the popup manager setting, the pop up windows can’t be larger than the viewable desktop areas.
• You can block all popup windows regardless the zone and user actions and use ALT key when you click on a link to show the pop up.
Developer implication
It affects
window.open(),
window.showModelessDialog(),
window.showModalDialog(),
window.navigateAndFind()
and window.showHelp() methods
When you write code to launch popup and the function should return a window object then it will return null and exception will be fired.
You should use try/catch or use window.onerror to catch the exception that happened when the popup launch failed.
You can find more fine tuning options in this key
HKEY_LOCAL_MACHINE\Software\Microsoft \Internet Explorer\Window Restrictions\
Like the ability to show full screen windows
For application developers there’s COM interface called INewWindowManager that allows applications that uses rendering engine in IE to use the popup manager
For more information
https://msdn.microsoft.com/security/productinfo/XPSP2/securebrowsing/popup_devimp.aspx
Miscellaneous
Windows XP Sp2 also contains updates to the windows update service and the software update services. For more information please read these documents
KB articles and how to
How to enable remote administration to windows xpsp2
These administrative options listed below can administer remote machine
· Certificates
· Computer Management
· Device Manager
· Disk Management
· Event Viewer
· Group Policy
· Indexing Service
· IP Security Monitor
· IP Security Policy
· Local Users & Groups
· Removable Storage Management
· Resultant Set of Policy
· Services
· Shared Folders
· WMI Control
In addition to the MMC snap-ins, these dialog boxes and administrative tools are affected:
· Select Users, Computers, or Groups
Find Users, Contacts, and Groups
· Net.exe
If you receive error messages like “Access denied “ or “network not available” then you need to open tcp port 445 in the remote machine.
Resolution
To open the port using command prompt, type:
netsh firewall set portopening TCP 445 ENABLE
How to enable remote debugging with SP2
ASPNET Cannot Serve Pages When Running on XPSP2
Primary Common issue associated with:
Windows Firewall
Scenario / Issue
ASP.NET pages might be inaccessible when you want to serve pages to remote clients from a server running XPSP2.
Summary of Resolution
In order to serve pages to a remote HTTP client , the user needs to add inetinfo.exe to the exceptions list. This is the recommended solution. Alternatively, you can enable the HTTP and HTTPs ports on the XPSP2 machine running ASP .NET. The default port for HTTP is port 80. The default port for HTTPs is port 443.
ASP.NET session state pages might not work on XPSP2
Primary Common issue associated with:
Windows Firewall
Primary Audience issue associated with:
DSV
Scenario / Issue
ASP.NET session state pages might not work if they are configured to use the ASP.NET StateServer or SQLServer session state mode and the StateServer or SQL Server is running on a remote machine with Windows Firewall turned on.
Summary of Resolution
For ASP.NET Session State pages involving remote StateServer or SQLServer, the Windows Firewall (WF), if enabled, needs to be modified with exceptions to enable ports used by StateServer or SQL Server.
Reproduction and Resolution Steps
The default port used by ASP.NET session state StateServer is port 42424. The default port used by SQL Server is port 1433. This is also true for other data access to SQL Server. The administrator needs to ensure that the application can access the port the remote SQL Server is using.
ASP and ASP.NET may not work if IIS is installed After Windows XP SP2
Primary Common issue associated with:
Distributed Component Model (DCOM)
Primary Audience issue associated with:
DSV
Scenario / Issue
If MSDTC is not running as NetworkService then ASP and ASP. NET will not work on a Windows XP SP2 machine. MSDTC might not be running as NetworkService if IIS is installed AFTER you install Windows XP Service Pack 2.
You might receive the following error when accessing a web page from this machine:
[The page cannot be displayed
The page you are looking for is currently unavailable. The Web site might be experiencing technical difficulties, or you may need to adjust your browser settings.]
WinSE 69962
Summary of Resolution
To resolve the issue you must uninstall MSDTC, clean the registry entries for MSDTC then reinstall IIS.
Reproduction and Resolution Steps
Steps to resolve the issue.
From the command line issue a 'Net stop msdtc' command.
From the command line issue a 'msdtc -uninstall' command.
Using Regedit, delete the key, including all of its subkeys and values, HKLM\Software\Microsoft\MSDTC.
From the command line issue 'msdtc -install'.
From the command line issue 'net start msdtc'.
Uninstall IIS.
Reinstall IIS.
Enabling ASP.NET Transactions with Windows XP SP2
Primary Common issue associated with:
Distributed Component Model (DCOM)
Primary Audience issue associated with:
DSV
Scenario / Issue
ASP.NET pages that rely on transactions might not work if they involve coordination with a remote machine. A user might get the following exception in this case:
[COMException (0x8004d024): The transaction manager has disabled its support for remote/network transactions.]
or page loading might timeout with a “Server Unavailable” message.
Summary of Resolution
For transaction pages involving a remote machine to work, the MSDTC needs to be configured to allow “Network Transactions” and any other associated properties, and the Windows Firewall (ICF), if enabled, needs to be modified with exceptions to allow communication with the remote machine involved in the transaction.
Reproduction and Resolution Steps
Configuring MSDTC:
- On the machine hosting the ASP.NET page open the Control Panel\Administrative Tools.
- In Administrative Toolsdialog box, open Component Services.
- In Component Services dialog box, click Component Services in the left panel.
- Double-click on the Computers folder in the right panel.
- Right click on My Computer and select Properties. If the Properties menu option is not available, click on the “My Computer” icon in the toolbar of the “Component Services” dialog.
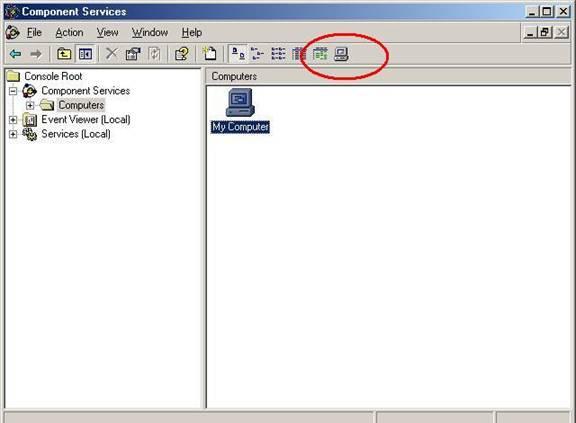
- From the My Computer Properties dialog, select the MSDTC tab.
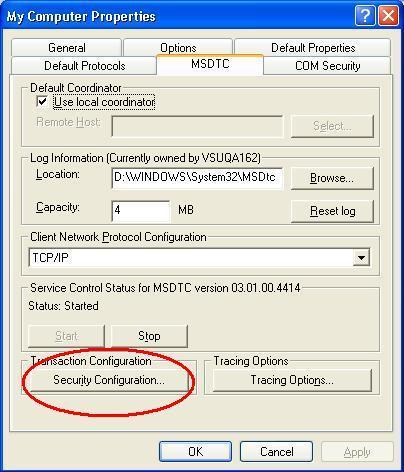
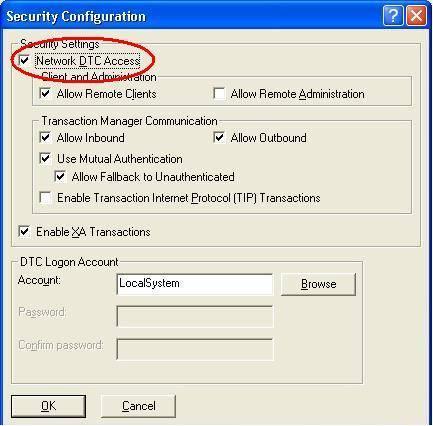
- Now click on Security Configuration. From the next dialog, you will need to enable Network DTC Access and any other settings your Transaction requiring page needs.
Configuring WF to allow MSDTC network traffic:
- To configure WF, Open the Control Panel.
- Open Security Centerthen open Windows Firewall.
- Select the Exceptions tab.
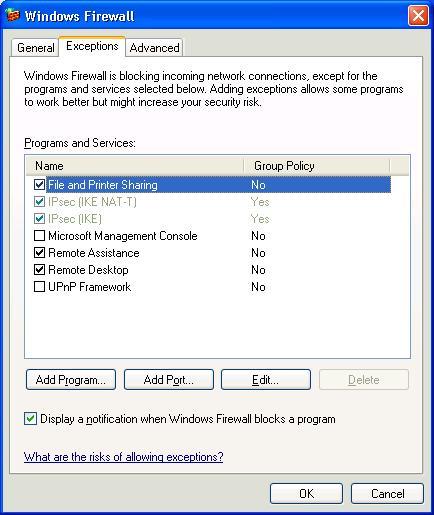
- Click on the Add Program button.
- Add a program exception for MSDTC by selecting the browse button and browsing to “msdtc.exe” (system32 directory).
Enabling COM Logging to assess permissions for DCOM Launch/Activation with Windows XP SP2
Primary Common issue associated with:
Distributed Component Model (DCOM)
Primary Audience issue associated with:
DSV
Scenario / Issue
Customer upgrading to SP2 will need to understand how to troubleshoot permissions issues concerning activation and call failures. With SP2 DCOM Launch/Activation and Access permissions have become more granular allowing you to specify permissions for accounts to have access locally and remotely.
Summary of Resolution
In order for customers to assess what permissions need to be added, they can add the following keys to the registry to add additional COM logging to the event log:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole]
"ActivationFailureLoggingLevel"=dword:00000001
"CallFailureLoggingLevel"=dword:00000001
When you have logging enabled, you will see logging as follows for Access and Activation permission issues:
Event Type: Error
Event Source: DCOM
Event Category: None
Event ID: 10014
Date: 5/26/2004
Time: 12:06:49 PM
User: NT AUTHORITY\ANONYMOUS LOGON
Computer: JCJONES-XP2
Description:
The machine wide limit settings do not grant Remote Access permission for COM Server applications to the user NT AUTHORITY\ANONYMOUS LOGON SID (S-1-5-7). This security permission can be modified using the Component Services administrative tool.
For more information, see Help and Support Center at https://go.microsoft.com/fwlink/events.asp.
Data:
0000: a0 01 00 00 00 00 00 00 .......
0008: c0 00 00 00 00 00 00 46 À......F
Event Type: Error
Event Source: DCOM
Event Category: None
Event ID: 10014
Date: 5/26/2004
Time: 12:06:49 PM
User: NORTHAMERICA\jcjones
Computer: JCJONES-XP2
Description:
The machine wide limit settings do not grant Remote Activation permission for COM Server applications to the user NORTHAMERICA\jcjones SID (S-1-5-21-124525095-708259637-1543119021-109255). This security permission can be modified using the Component Services administrative tool.
For more information, see Help and Support Center at https://go.microsoft.com/fwlink/events.asp.
Data:
0000: a0 01 00 00 00 00 00 00 .......
0008: c0 00 00 00 00 00 00 46 À......F
After reviewing the event log entries you will know what accounts need to be added for permissions to the COM server.
The NET SEND command may not work correctly on a computer that is running Windows XP Service Pack 2
https://support.microsoft.com/default.aspx?scid=kb;en-us;839018
You may not be able to connect to an instance of SQL Server that is configured to use the TCP/IP server network library on a computer that is running Windows XP Service Pack 2
https://support.microsoft.com/default.aspx?scid=kb;en-us;841394