Limit access to just Visual Studio Team Services using Azure Active Directory Premium
By leveraging Conditional Access Policies of Azure Active Directory (AAD) Premium it's possible to add external users to your AAD and limit them to just Visual Studio Team Services (VSTS).
You'll need:
- An Azure subscription
- AAD Premium (you can get a trial if you just want to try this out)
- A VSTS account backed by the Premium AAD
- An external user you can invite to your AAD \ VSTS (someone not native to the AAD)
Here's how I set up a demo (pictures below, too):
- In Portal.Azure.com, enabled AAD Premium on ConditionalVSTS.onmicrosoft.com
- Created a native AAD user - ROOT@ConditionalVSTS.onmicrosoft.com - who was a global admin
- Invited SomeExternalDude@Outlook.com to the AAD and accepted that invite via mail at Outlook.com
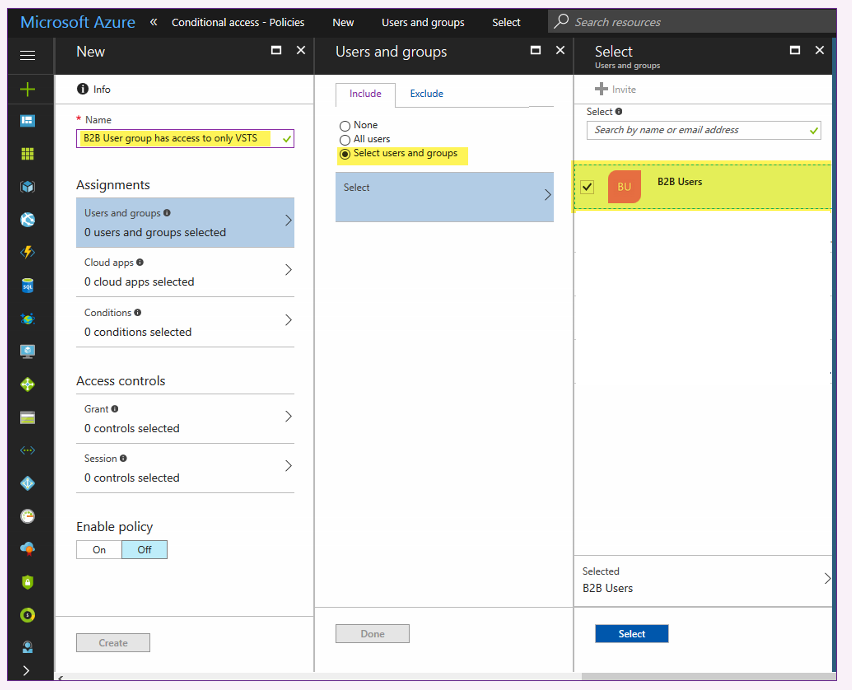
- Back in Portal.Azure.com, created an AAD group named "B2B Users" and added SomeExternalDude@Outlook.com to it
- Logged into aka.ms/getvsts as ROOT@ConditionalVSTS.onmicrosoft.com and created a new VSTS account. Because I logged in there as a member ConditionalVSTS.onmicrosoft.com, my new VSTS was backed by that AAD when it was created.
- Logged into my VSTS as ROOT@ConditionalVSTS.onmicrosoft.com (the owner) and added SomeExternalDude@Outlook.com to it, on the Users Hub
- In a different browser (not another instance, but another software browser) I logged into VSTS as SomeExternalDude@Outlook.com successfully. This was just to confirm all was working up to this point.
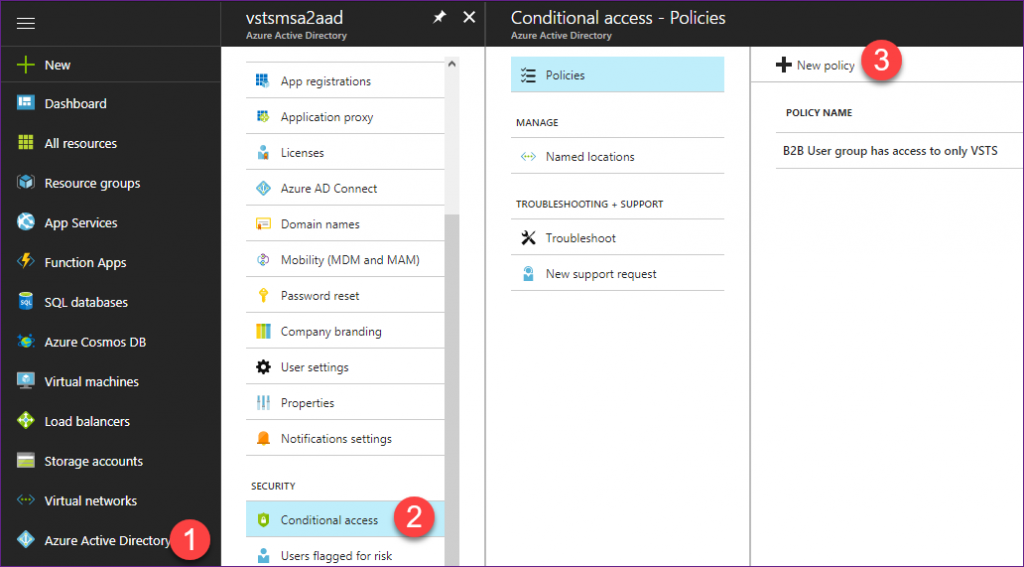
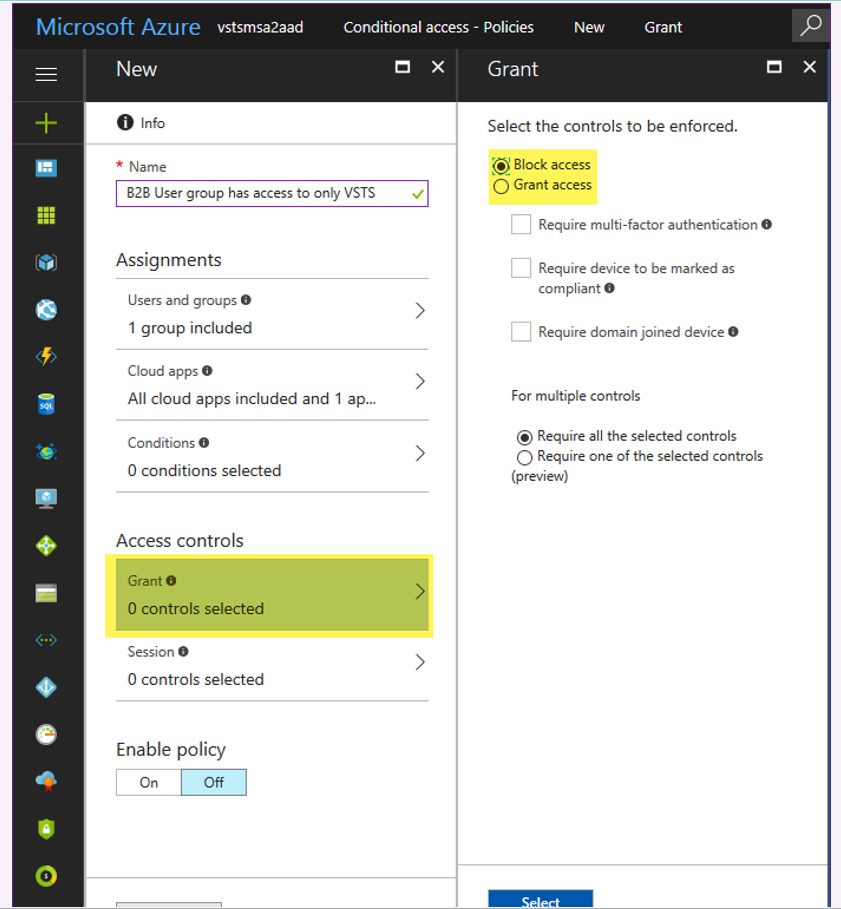
- Back in AAD on Portal.Azure.com I set up a new Conditional Access Policy designed to permit SomeExternalDude@Outlook.com to *only* access VSTS. Screen shots below.
- With the Conditional Access Policy enabled, back in my VSTS browser instance as SomeExternalDude@Outlook.com I signed out and then tried to sign back in. Still worked.
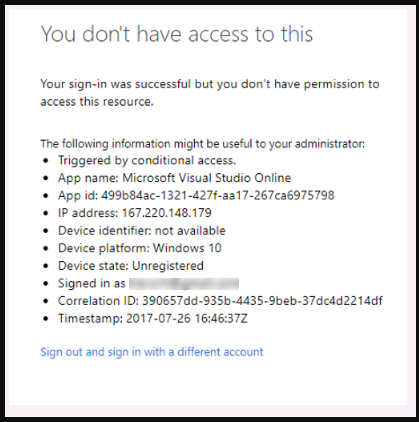
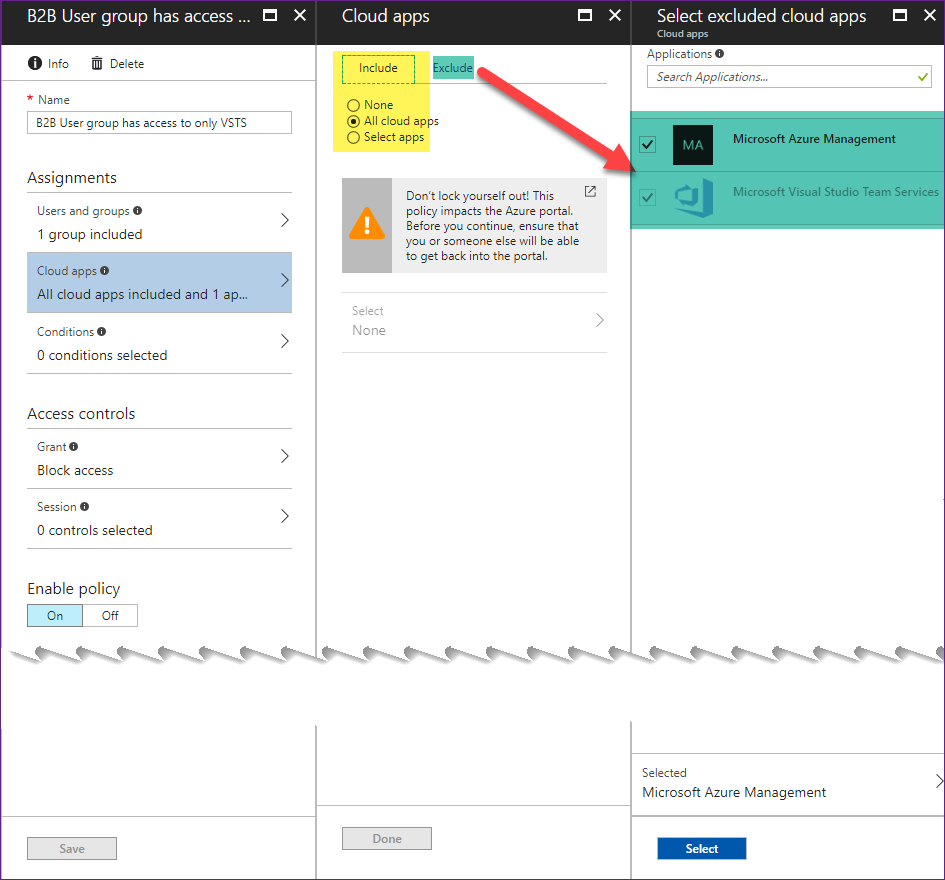
At this point you might be wondering what's the point? Well, to see what happens when VSTS & Microsoft Azure Management are *not* included in the exceptions list for that Conditional Access Policy, edit it and remove them. The next time any member of the "B2B Users" group tries to log into a VSTS account backed by that AAD they'll see something like the message pictured below ("You don't have access to this") .
You can use a variation on this process to let AAD groups into only VSTS, or let them into everything but VSTS.
I hope you find this helpful.
--TrevorH
References:
- Intro to Microsoft Azure AD Premium
- Get started with conditional access in Azure Active Directory
- Team Services: Access with Azure Active Directory (Azure AD)
- Manage conditional access to Team Services
Azure AD Conditional Access Policy to let members of AAD group "B2B Users" access *only* VSTS