Federated Identity interoperability samples
Customers frequently ask me about interoperability with their non-Microsoft products, and identity is not an exception. There’s roughly 2 set of scenarios that come up often:
- A relying party (an application) built on the Microsoft stack trusting a non-Microsoft Identity Provider.
- A non-Microsoft application trusting ADFS.
Good news in the identity world is that there are quite some standards that we all have agreed to implement (WS-Federation, SAML, WS-trust, etc). A few weeks ago I reached to to my colleague Claudio Caldato, who is a member of our Interoperability Labs and has spent quite some time figuring out all the implementation details of these scenarios.
Claudio was kind enough to allow us to use his lab, so we’ve been busy deploying one of our apps from the Guide there and learning from the process.
More good news: everything works with zero changes to the app :-).
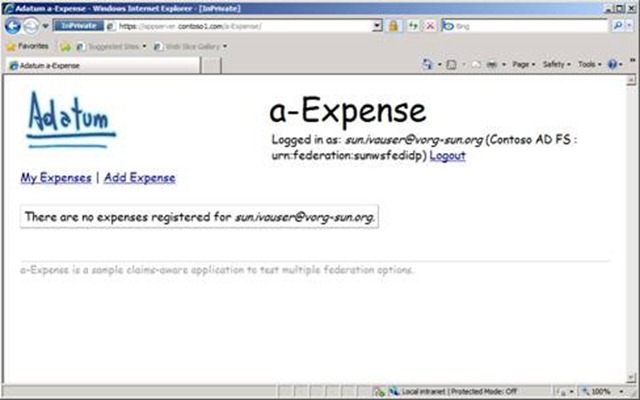
Here’s a screenshot of a-Expense with a user authenticated on an OpenSSO identity provider (you can only tell from username):
Claudio’s lab is quite comprehensive and we have this running against IBM Tivoli Manager, CA Siteminder and Oracle’s identity products too.
Stay tuned, we’ll post more information soon.