Getting Started with Windows 10 Device Guard - Create Code Integrity Signing Certificate
Back to Getting Started with Windows 10 Device Guard – Part 2 of 2 contents
Getting Started with Windows 10 Device Guard - Create Code Signing Certificate
To sign our catalog, we require a code signing certificate. On the certificate authority open up the snap-in by running the following command.
certsrv.msc 
Expand the server, right click on the Certificate Template folder and select Manage.
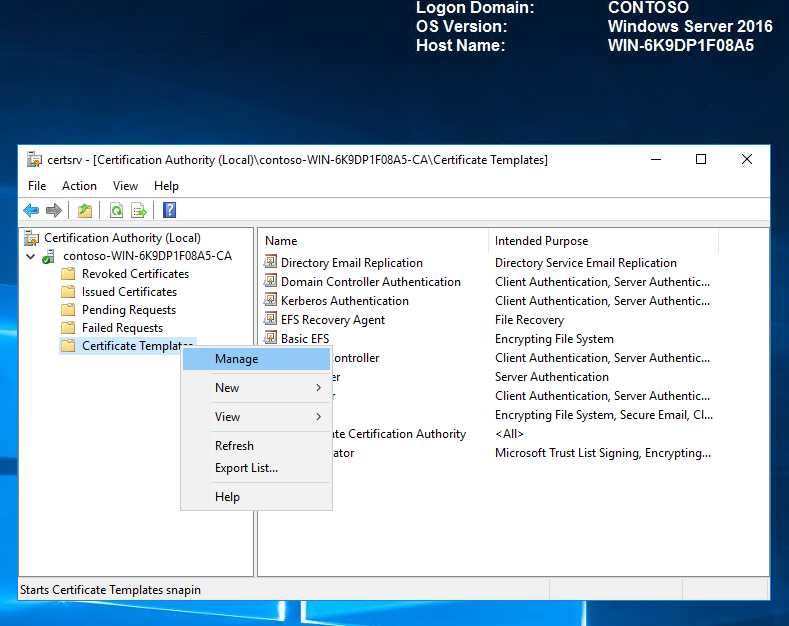
In the certificates template console, right click on the Code Signing template and click duplicate template.
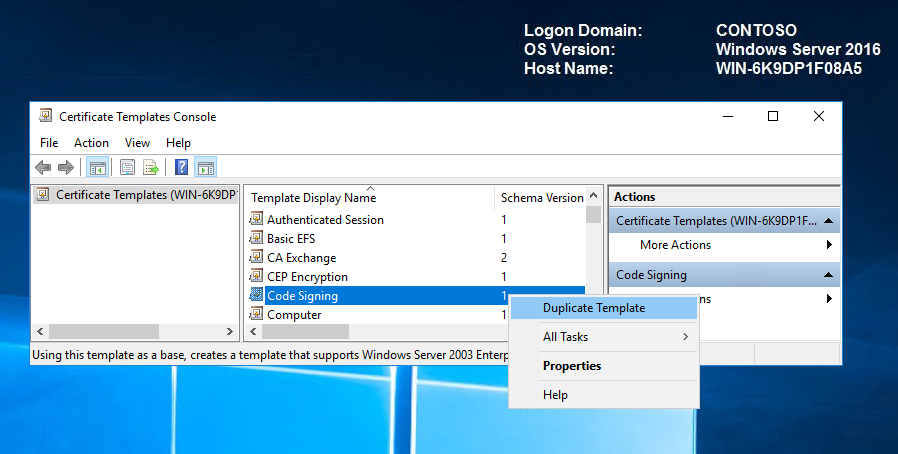
On the Compatibility tab, clear the Show resulting changes check box. Select Windows Server 2012 from the Certification Authority list, and then select Windows 8 / Windows Server 2012 from the Certificate recipient list.
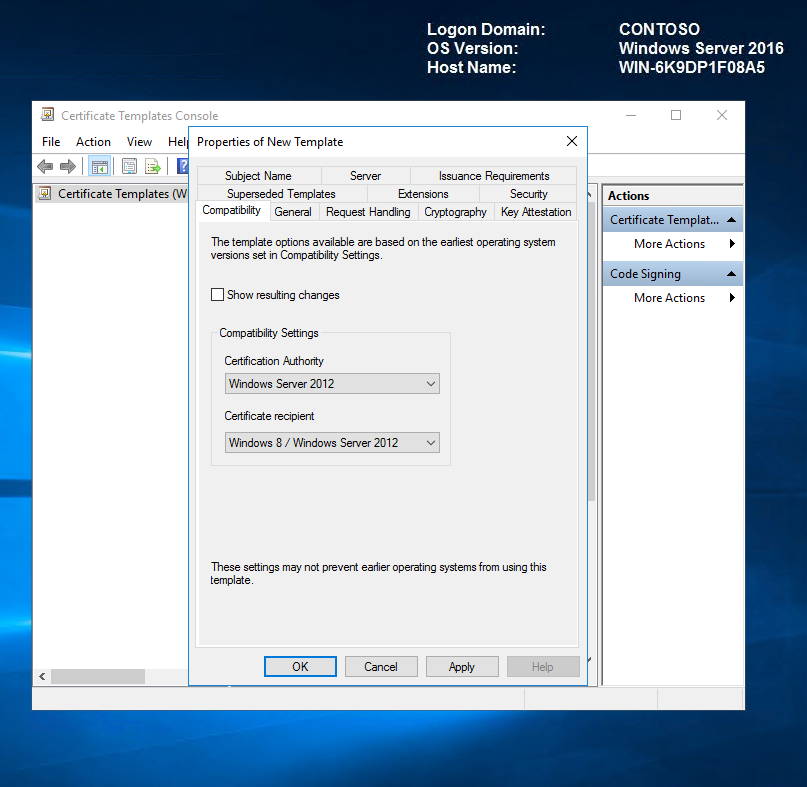
On the General tab, specify the Template display name and Template name. We will call it DG Catalog Signing Certificate.
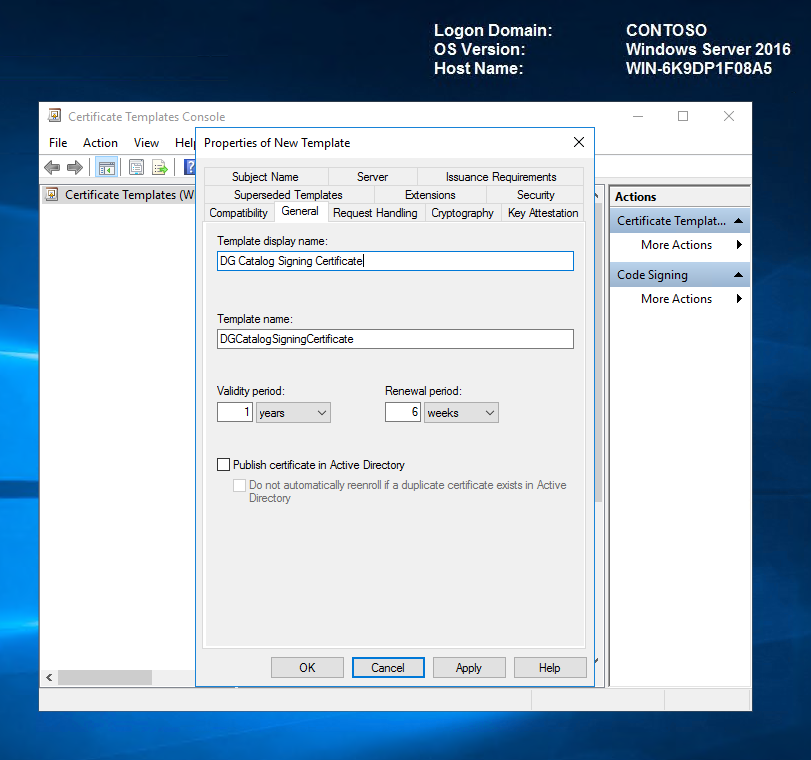
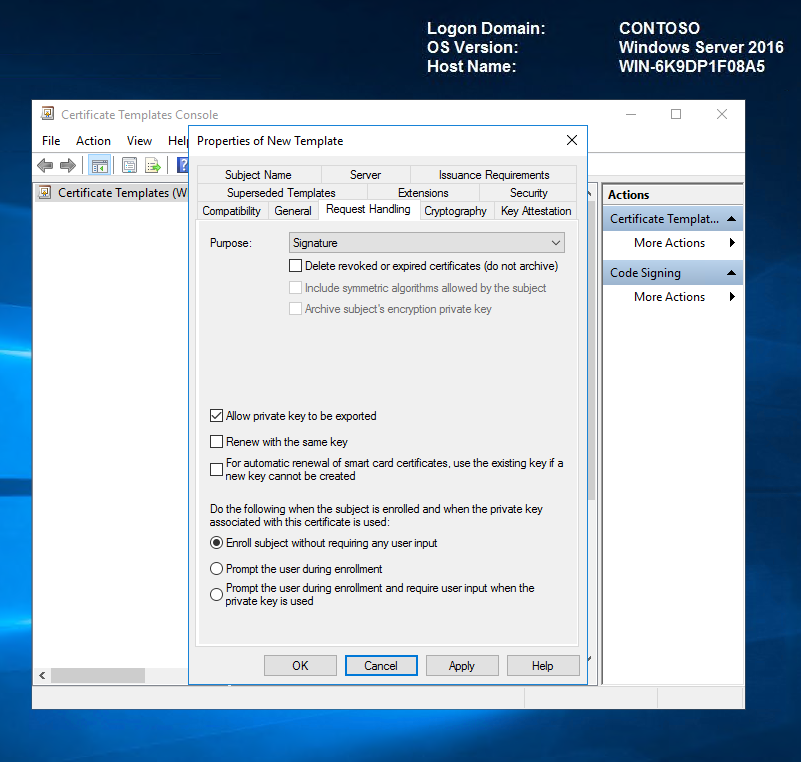
On the Request Handling tab, select the Allow private key to be exported check box.
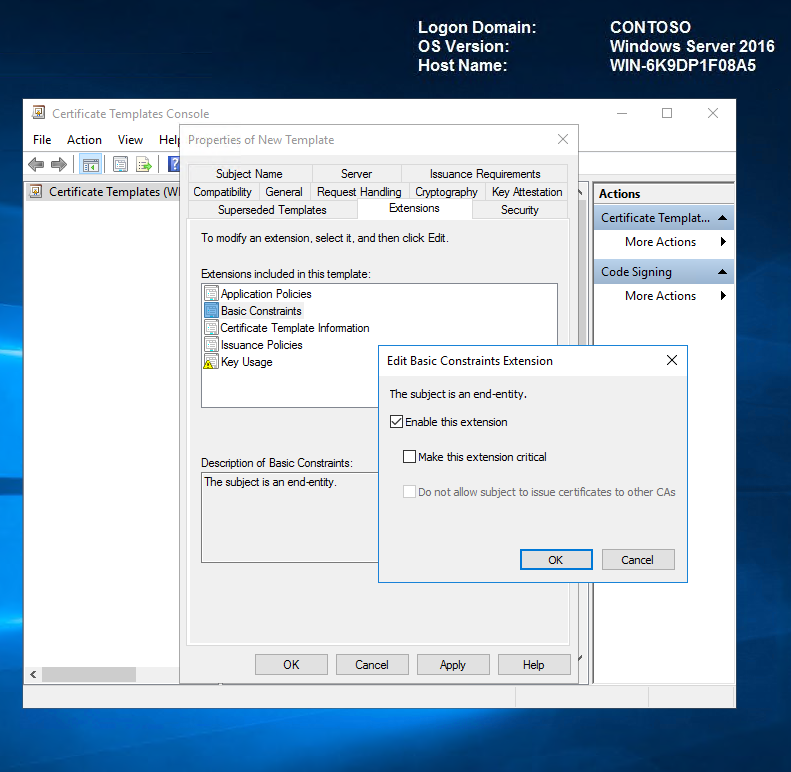
On the Extensions tab, select the Basic Constraints check box, and then click Edit. In the Edit Basic Constraints Extension dialog box, select Enable this extension.
If a certificate manager is required to approve any issued certificates, on the Issuance Requirements tab, select CA certificate manager approval.
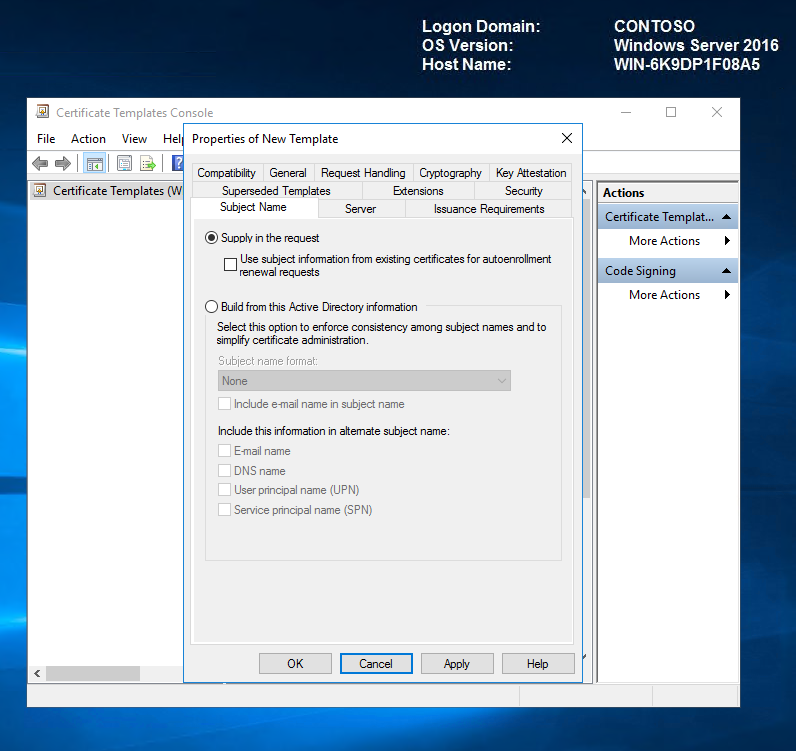
On the Subject Name tab, select Supply in the request.
On the Security tab, verify that whatever account will be used to request the certificate has the right to enrol the certificate. We will leave the defaults but you can granulate as you see fit.
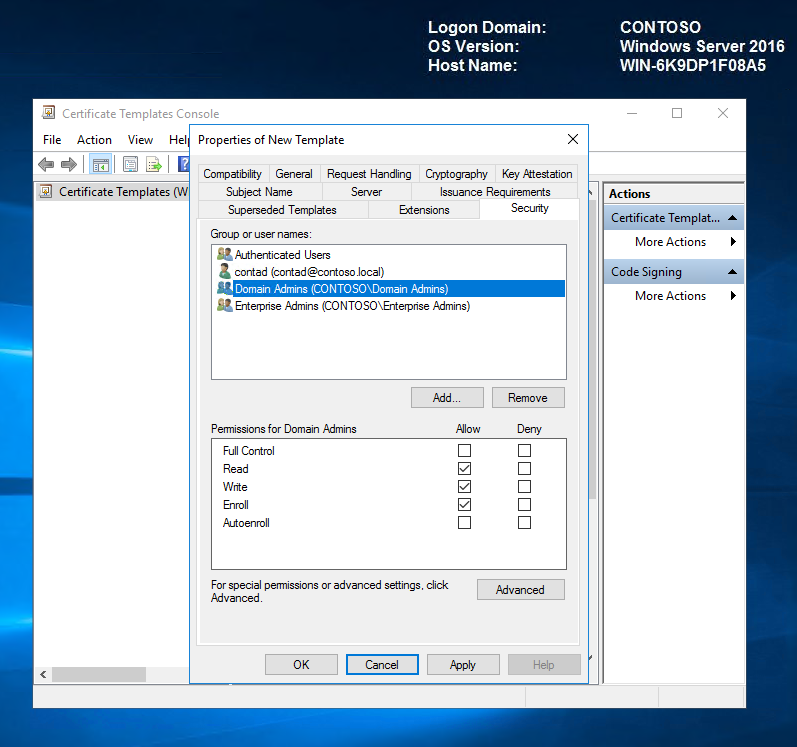
Click OK to create the template, and then close the Certificate Template Console.
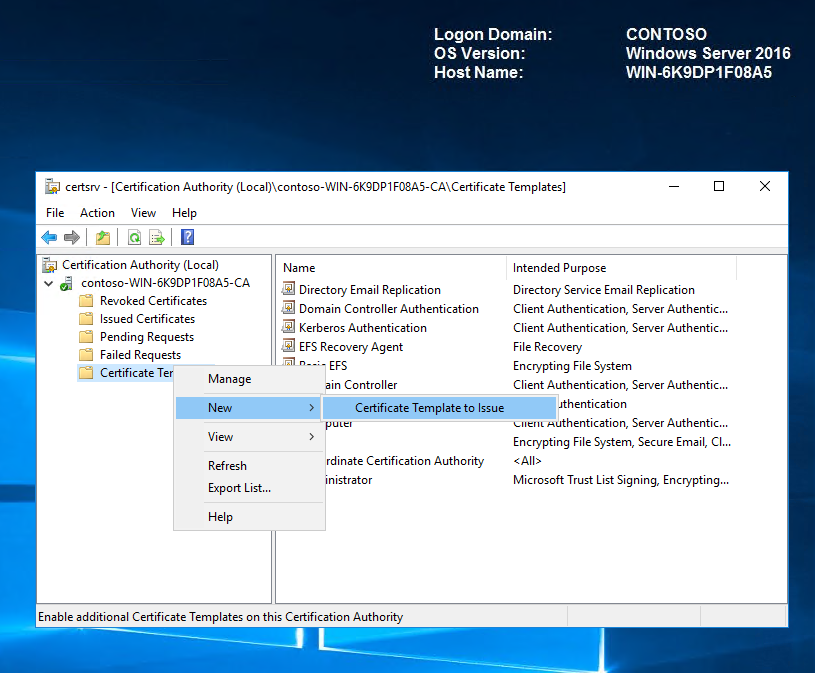
Now that we have created the code integrity certificate template, we must publish it to the CA published template store. To do so, we will right-click Certification Templates, point to New, and then click Certificate Template to Issue.
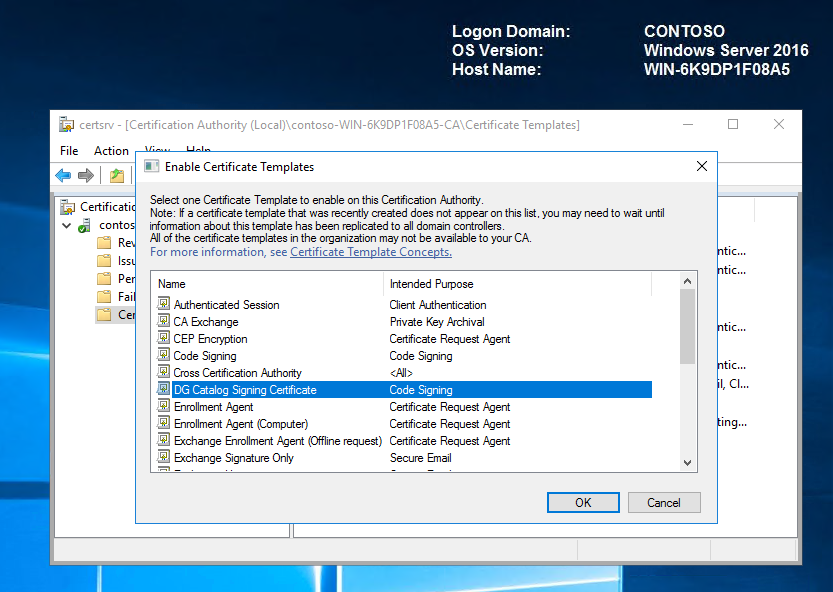
Select the DG Catalog signing certificate, and then click OK.
Now that the template is available to be issued, we must request one from the computer running Windows 10 on which we will create and sign catalog files, in our case, this will be our GOLD-MACHINE.
On GOLD-MACHINE, type MMC in a run box, from the File menu, click Add/Remove Snap-in. Double-click Certificates, and then select My user account.
In the Certificates snap-in, right-click the Personal store folder, point to All Tasks, and then click Request New Certificate.
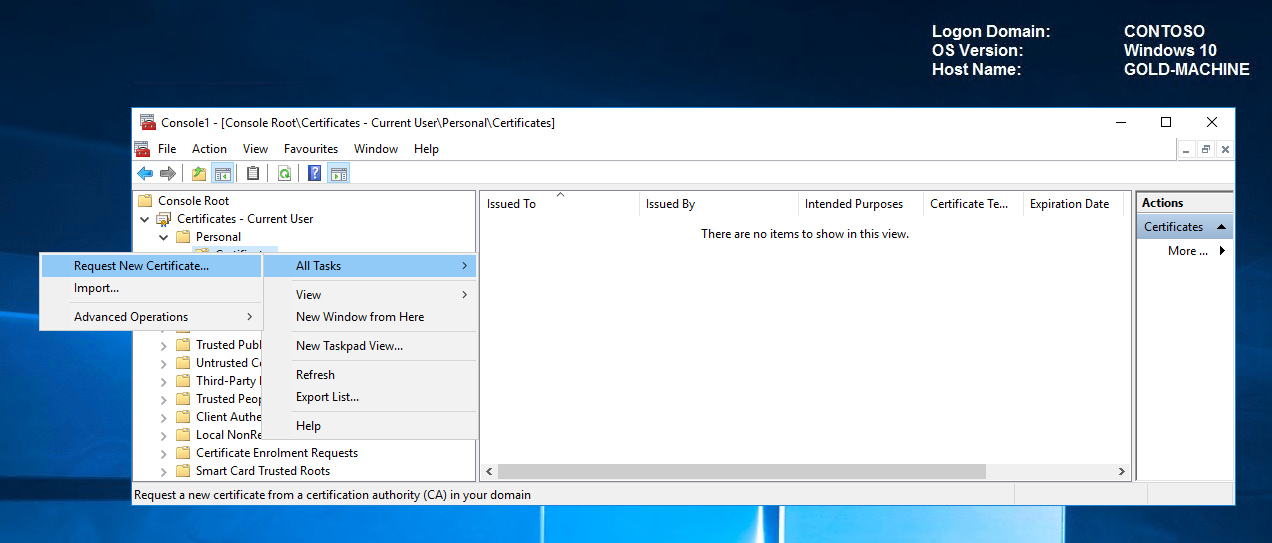
Click Next twice to get to the certificate selection list. In the Request Certificate list, select your newly created code signing certificate, and then select the blue text that requests additional information.
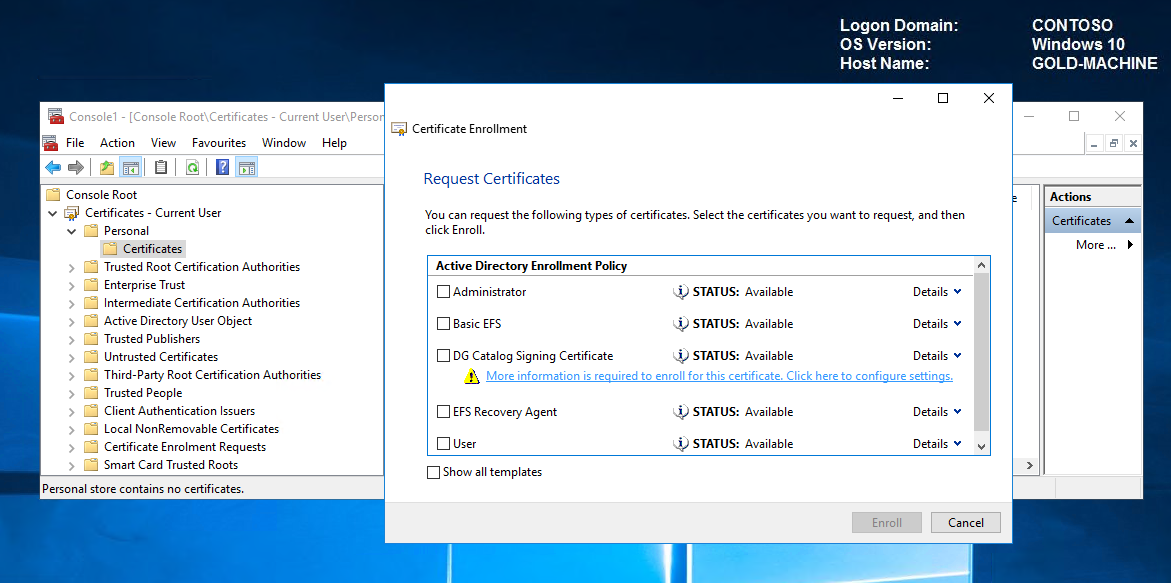
In the Certificate Properties dialog box, under Subject Name, for Type, select Common name. For Value, select ContosoDGSigningCert, and then click Add.
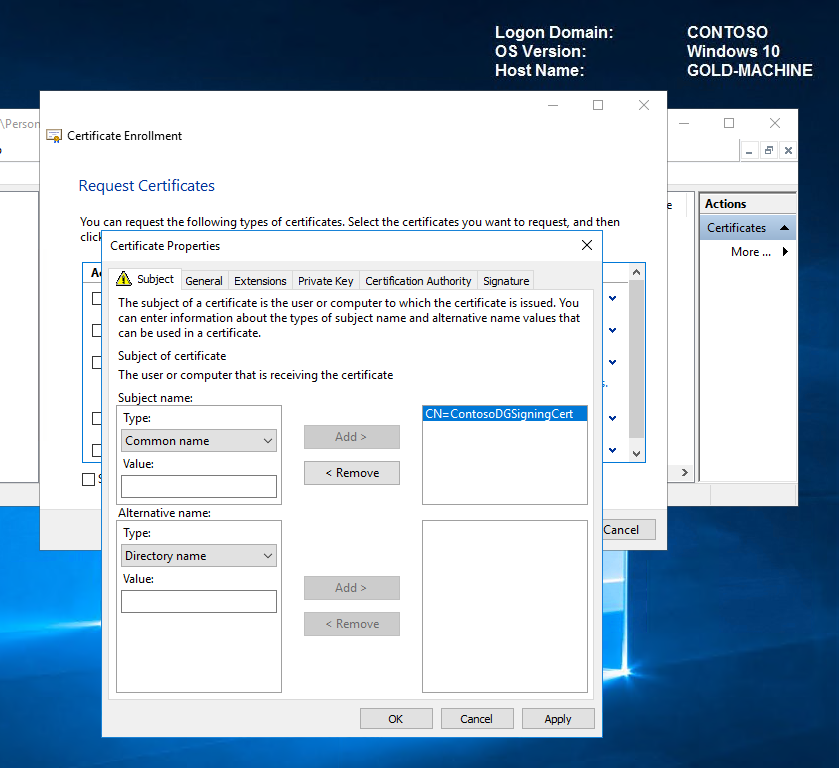
Select the certificate and click Enroll.
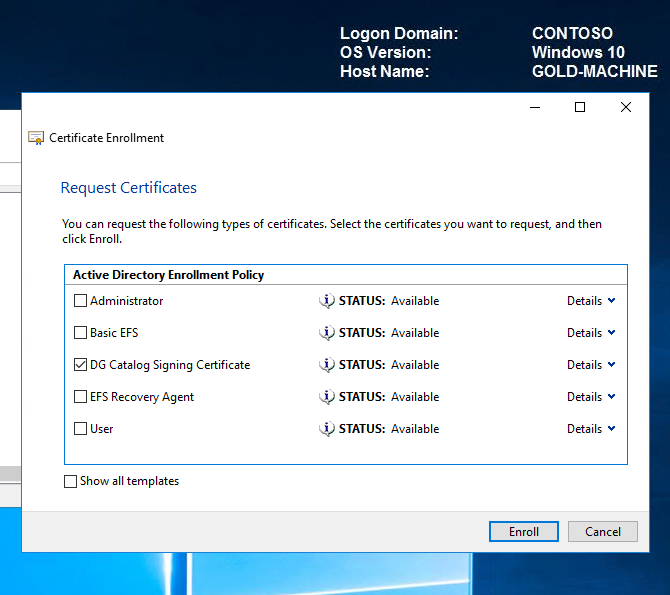
On successful enrolment, click Finish.
Let's navigate to our certificate personal store to verify that we now have our new ContosoDGSigningCert certificate. Open a MMC snap-in, click file, add/remove snap-in, select certificates in the left hand pane and click add. When prompted, select user account.
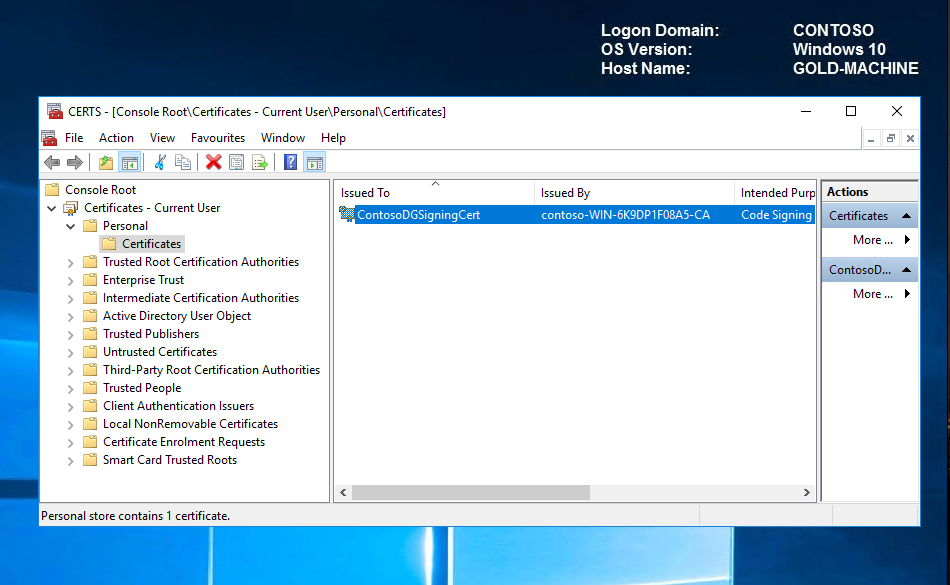
Note The certificate must be installed in the user’s personal store on the computer that will be signing catalog files and/or code integrity policies (in our case GOLD-MACHINE). Because the signing is going to take place on the computer that we just requested the certificate on, we don't need to export the certificate as it already exists in our personal store. If you are signing on another computer, you will need to export the .pfx certificate with the necessary keys and properties and secure using a strong password. When the certificate has been exported, import it into the personal store for the user who will be signing the catalog files or code integrity policies on the specific computer that will be signing them.
Important Note
Be sure to backup and protect your PKI infrastructure.
Chris Ayres has written a great blog that's really worth checking out!
https://blogs.technet.microsoft.com/paranoidhumanoid/2015/09/15/certificate-services-disaster-recovery/
Back to Top Back to Getting Started with Windows 10 Device Guard – Part 2 of 2 contents